As you know, I’m a big fan of being a subject matter expert (SME) of the data you are analyzing. If you are analyzing payroll data, learn about it. But if you are dealing with encryption in data science, you will want to take this online cryptography course.
Go to course!
Reasons for Data Scientists to Take this Online Cryptography Course
- To learn why and how cryptography is used
- To learn the processes that take place in cryptography
- To learn the vocabulary words used with cryptography
- To anticipate the type of data involved in studying encryption – such as doing hacking forensics
Online Cryptography Course Teaches the “Why and How” of Cryptography
In the beginning, the author, Stephanie Domas, describes that she does ethical hacking to test medical devices to protect them from getting hacked. She says the best way to prove yourself as an ethical hacker is to pass the certified ethical hacker exam. This online cryptography course teaches the cryptography topic on the exam, so you can pass that.
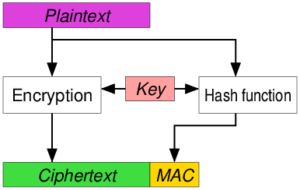
Cryptography is converting data to a scrambled form in such a way that you can unscramble it if you know how. Before we get to into the topic, we should ask ourselves: why are we scrambling the data in the first place?
Personally speaking, my customers scramble their data because – well – they don’t mean to. Then, they come crying to me for help, and I provide “data therapy”. I say look on the bright side – your data are such a mess, it doesn’t matter if you get hacked!

But seriously, scrambling data in cryptography – in other words, scrambling data on purpose in such a way that you can unscramble it later – has four main uses that are covered in this online cryptography course:
- Authentication – You can use cryptography to prove who you are.
- Integrity – You can use cryptography to prove data have not been altered.
- Confidentiality – You can restrict access using cryptography.
- Non-repudiation – You can confirm receipt of identity of sender and data using cryptography

Hot Data Science Tip
For data scientists, probably the most important part of this online cryptography course is Chapter 6, where the author describes encrypting data at rest (DAR) and disk encryption.
Learn about Management Issues from this Online Cryptography Course
Leadership choices made related to encryption seems like they could greatly impact your work as a manager. I made a list of some managerial issues that are covered in the course, and these provide some hints as to how much work it is if your job is to manage cryptography efforts in your organization:
Chapter 1
Chapter 1 describes the effort associated with tracking keys if you choose symmetric encryption for your organization.
Chapter 2
Chapter 2 examines weighing the ease of processing and issues with privacy aspects associated with symmetric ciphers against the computationally-intensive but more secure asymmetric ciphers.


Chapter 3
Chapter 3 talks about how hashing is used in encryption, and the pros and cons of choosing various hashing algorithms so as to avoid collisions.
Chapter 4
Chapter 4 explains what digital certificates are, how to get them, what data define them, how to track and manage them, and what role they play in trust models.

Chapter 5
Chapter 5 covers practical issues with managing digital certificates within the Public Key Infrastructure (PKI). The videos include some excellent flow charts demonstrating actual steps in applying trust models.
Chapter 6
Chapter 6 shows how these concepts are applied, and is probably most useful and imaginable to the data scientist.

Chapter 7
Chapter 7 breaks down how hackers launch cryptographic attacks using diagrams to indicate which part of the cryptographic process they are hacking and how. It also calls out real-life examples of newsworthy cryptographic attacks.

Hot Data Science Tip
Like with longer passwords, longer keys are more secure against cryptography attacks.
- What hashkeys and hash collisions are, and how to do cryptographic hashing
- Why the XOR Cipher is so controversial
- How the Caesar Cipher got its name
- Where the terms Rijndael and Rivest came from
- What was invented in 1976 by Whitfield Diffie and Martin Hellman
- What a trapdoor function is and how you can fall into one
- What happens when a malicious actor gets into the trusted circle (spoiler: Don’t trust Bob!)
- How a certificate can get on the revocation list
- What GAK stands for and why we have GAK
- Why FTP, SMTP, HTTP and telnet are “protocol no-nos” nowadays (even though old hands like me are forced to admit we used to use them all the time!)
- What happens when you go to a web site with an invalid certificate and choose to “proceed” anyway, and the seedy (and not-so-seedy) reasons it might be invalid
- How to remotely hack someone else’s account by replaying a hash
- What Deep Crack is, how much it costs, and what it did
- The backstories behind Heartbleed, POODLEbleed, DROWN, and FREAK (Who names these things??)
Get Important Terminology from this Online Cryptography Course
The author also spills the tea on some hot cryptographic gossip!
Go to CourseWant to better understand marketing analytics? I recommend taking this online marketing foundations course from LinkedIn Learning.
Updated November 11, 2020. Encryption diagram by RokerHRO, available here. Anarchist hackers banner by REK2, available here. Most delicious picture of Indian eggs by Vmalvjay, available here. Picture of computer hacker by wwward0, available here. Gorgeous photograph of Minneapolis skyline by Tony Webster from Minneapolis, Minnesota and available here.
Even if you do not deal directly with cryptography, the need to maintain data privacy often leads data scientists to need to study cryptography. This basic online course is part of an ethical hacking certification and gives a basic overview of issues with data transfer and cryptography.


